Vijay Pasupathinathanipsa scientia potestas est
Introduction
The ease of purchasing and selling products over the Internet has helped the growth of electronic commerce and electronic payments services are a convenient and efficient way to do financial transactions. Current e-payment technologies depend on using traditional methods that are common to non-electronic systems. Due to the nature of Internet, security and authenticity of payments and participants cannot be guaranteed with technologies that are not specifically designed for electronic commerce. We need an e-payment system that would not only provide secure payments but should also have properties like online customer and merchant authentication, unforgeable proof of transaction authorisation by the customer both to the merchant and the bank, privacy of customer and transaction data. This chapter provides an overview of e-payment architecture and their functionalities, their requirements and verification of payment protocols. More thorough survey can be found in [1] [2] [3] [4] [5] [6] [7] and [8].
Generic E-Payment System
1. Entities
Electronic payments involve a payer and a payee. A payer (buyer or customer), is an entity who makes a payment. A payee (seller or merchant), is an entity who receives a payment. The main purpose of an electronic payment protocols is to transfer monetary value from the payer to the payee. The process also involves a financial institution (bank or mint).
Typically, financial institution participates in payment protocols in two roles: as an issuer (interacting with the payer) and as an acquirer (interacting with the payee). The issuer is responsible for validating the payer during account registrations and holds the payer’s account and assets. The acquirer holds the payee’s account and assets. The payee deposits the payments received during a transaction with the acquirer. The acquirer and the issuer then proceed to perform an inter-banking transaction for clearance of funds. It is possible for the issuer and the acquirer to be from the same financial institution.
Other parties that may be present in a payment protocol include a Trustee (arbiter) who is an entity that is independent from all parties. All entities in a protocol unconditionally trust the Trustee who is called to adjudicate any disputes between the payer and the payee. Certain payment systems might involve more players like Payment Gateways (PG) who are entities that act as a medium for transaction processing between other entities (e.g. MasterCard, Visa) and Certification Authorities (CA) who are necessary if the e-payment systems involve PKI’s. They issue public key certificates to entities involved in a payment protocol so that their authenticity can be publicly verified. Figure 1 illustrates the participating entities in an e-payment system.
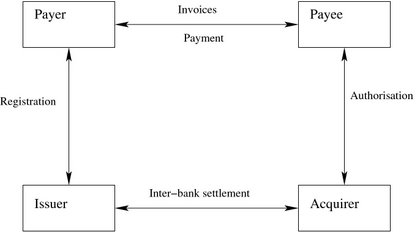
Figure 1: Generic E-payment Protocol
2. Phases in E-Payment
An electronic payment typically involves the following phases:
- Registration: This phase involves the registration of the payer and the payee with the issuer and acquirer respectively. Most electronic payments designed require registration of payers and payees with their corresponding banks so there is a link between their identities and their accounts held at the bank.
- Invoicing: In this phase, the payee obtains an invoice for payment from the payee. This is accomplished by either browsing and selecting products for purchase from the merchant’s (payee’s) website in case of purchases made through the internet or obtaining an electronic invoice using other electronic communication medium like e-mail. This phase typically is performed in an unsecured environment and normally excluded while designing payment protocols. The importance of this phase is that, it sets the mandatory and optional data variables that should be included in a payment protocol.
- Payment selection and processing: In this phase the payer selects type of payment, (card based, e-cash, e-cheque, etc.,) based on the type of payment the payee accepts. Based on the selection, the payer then sends the relevant payment details like account number, unique identifiers of the payer to the payee along with accepted amount based on the invoice. Certain protocols might also require the payer to obtain preauthorised token (like bank drafts) from the issuer before the payer sending the payment information to the payee.
- Payment authorisation and confirmation: In this phase, the acquirer on receiving payment details from the payee authorises the payment and issues a receipt containing the success or failure of the payment to the payee. The payee based on the message may also issue a receipt of payment to the payer.
Classification of Payment Systems
As previously mentioned, electronic commerce can be broadly categorised into two groups, business-to-business (B2B) and business to consumer (B2C). B2B normally involve higher value transactions and predominant payment methods are electronic cheques and bank transfers, whereas, B2C payments are lower value transactions and payment methods used are cash and card based payment systems. This section presents an overview of e-payment classifications.
Payment instruments: There are three common electronic payment instruments, namely cash, cheque and card. Cash payment systems consist of self-authenticating divisible tokens that can be processed offline. Cheque payment system is typically linked to a payer’s account and payment is indivisible. Card payment schemes provide a payment mechanism through the existing credit card payment infrastructure.
Pre-paid, Pay-now and Post-pay: In pre-paid system the payment is debited from the payer’s account before a payment is processed and hence the term “pre-paid”. Most cash-like systems such as an electronic-cash system [9] [10] fall in this category. In pay-now system, when an electronic transaction is processed, the payer’s account is debited and the payee’s account is credited with the payment amount. Even though availability of funds depends on the time when inter-bank settlements are carried out, the payer’s and payee’s account are updated to show the debited and credited balances immediately after an transaction is carried out. Credit card based system, like Secure Electronic Transaction (SET) [11], Verified by Visa (VBV) [12], MasterCard secure-code [13] fall into this category. In post-pay systems the payer’s account is debited only when the payee’s makes a request for payment settlement with the acquirer. Most cheque based systems [14] [15] fall into this category.
Offline and Online: Based on communicational characteristics, electronic payments systems are classified as offline and online systems.
In an offline system, the communication does not involve any third party, i.e., an electronic transaction takes place only between the payer and the payee. The advantages of offline payments are lower communication cost and less time-critical transaction handling at the banks. However, they suffer from one serious drawback, the problem of double spending. Double spending occurs when the payer spends the same electronic money multiple times. In a digital system the payer could make a backup of electronic money before each payment and reset his system to this backup after the payment. In this way, an arbitrary number of payments to different recipients are possible with the “same” money.
Typically, double spending is prevented with the use of tamper-resistant hardware e.g. a smart card. In certain cases, the tamper-resistant hardware is issued by the bank containing a pre-authorised value of money. However tamper-resistant devices only offer limited protection as they are vulnerable to attacks [16] [17] [18]. Another way to prevent double spending is pre-authorisation. The payer obtains pre-authorised secure digital money from its bank, thus the payee is assured of payment e.g. a bank cheque. However, this method can only be used if the payee is known to the payer before a payment. A weaker solution, rather than employing prevention techniques is to detect double spending when they occur and the dishonest payer can be held accountable. This solution is used in most e-cash implementations. Adequate security can be achieved by a combined approach that would involve both detection methods and tamper-resisted devices.
In an on-line system, the payee typically connects to the bank to obtain a payment authorisation, thus increasing the communication requirements for the payment system. The advantage is, the payee obtains a guarantee on the payment, as the bank is able to authorise and check for availability of funds in the payer’s account.
Prepaid - Cash like system
The best-known subclass in pre-paid systems is the anonymous e-cash system introduced by Chaum [19] [20].
Basic model of e-cash system: An anonymous off-line e-cash consists of three probabilistic, polynomially-bounded parties, a bank B, payer P, and payee R, and three main sub protocols: withdrawal, payment and deposit (refer Figure 2). Payer and payee maintain their accounts with the bank. The payer withdraws electronic coins from their account with the bank, by performing a withdrawal protocol over an authenticated channel. The payer spends coins by participating in a payment protocol with the payee over an anonymous channel. In effect, the payee performs a deposit protocol, to deposit the coins into their account. The e-cash system also includes setup protocols: system setup, payer setup and payee setup which performs system initialisation functions, namely creating and publishing public keys and opening payer and payee bank accounts.
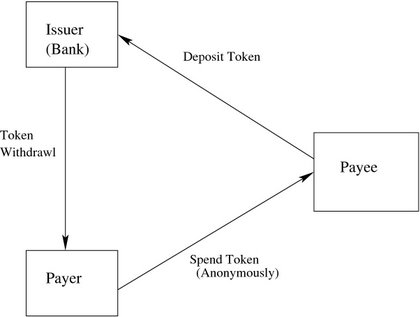
Figure 2: A Model E-cash system
Pay now or Card based system
The most common method for “on-line” payment is card-based systems. Most payment systems in this category are specifically designed for transaction conducted through the Internet. Because of their convenience and omnipresent nature, credit cards in particular have become a popular method for conducting online payments over the Internet, but they are insecure, offer no anonymity or protection of payer’s payment information like card details and account information. To overcome these drawbacks and make card payment more secure, the two leading credit card companies VISAand MasterCardhave developed various protocols. This section presents an overview of various card-based systems that have been proposed.
In 1995, Visa and Microsoft developed a card based system called as Secure Transaction Technology (STT) [24]. It featured strong, export-approved DES encryption of financial information, RSA encryption of bank account numbers, RC4 encryption of the purchasing order contents and receipts, and mandatory authentication of all participants. During the same time the IBM Research group proposed the Internet Keyed Payment Protocol (iKP) [25], which later became a part of MasterCard’s Secure Electronic Payment Protocol (SEPP) [26] proposal.
Due to the limited popularity of both STT and SEPP proposals, MasterCard and Visa in a joint effort proposed Secure Electronic Transaction (SET) [11] system that would take advantage of the combined customer and merchant base. SET was published as an open specification for the industry and the development of the payment system included major companies like GTE, IBM, Microsoft, Netscape, RSA, SAIC, Terisa and VeriSign. It incorporates digital signatures for not only authenticating customer but also merchants and banks. SET also included a unique concept known as dual signatures. The main goal of dual signatures is to protect the customer’s account information from the merchant and purchase information from the banks. Dual signatures link purchase information (like order message) sent to the merchant with the payment information (like account information) sent to the acquirer. When the merchant sends an authorisation request to the acquirer, it includes the payment information sent to it by the cardholder (customer) and the message digest of the purchase information. The acquirer uses the message digest from the merchant and computes the message digest of the payment information to check the dual signature. Even though the advantages of using SET are apparent, due to the system complexity, and implementation costs for both merchant and banks, the system has failed gain widespread market acceptance.
Today there are two major proposals for secure electronic payment over the Internet. They are Visa 3-D Secure [12] (Verified by Visa - VBV) and MasterCard SecureCode [13]. Both protocols rely on SSL [27] /TLS [28] to encrypt communication over the Internet. SSL is a client-server protocol that uses public key cryptography and has become the de facto standard for encrypted communication over the Internet. In SSL, only servers (merchants) have public key certificates and clients (buyers) remain anonymous to the servers. Because of the lightweight nature and an existing wider deployment base of SSL protocol, MasterCard and Visa have implemented a standard that would allow merchant to incorporate the proposed security features into their payment acceptance structure.
Pay later or Cheque based system
Customers generally tend to use credit card payment methods for low and middle value payments, whereas, cheque is the preferred method for large value payments. Various electronic cheque (e-cheque) protocols [29, 30, 31, 15, 21] have been proposed over the years. Systems like FSTC’s eCheck [15], NetCheque [30] and MANDATE II [29] are based on methods used in traditional paper based checking protocols. Systems like NetBill [31], ECheque and PayNow by CyberCash use a central server. Other e-checking systems are based on modified versions of e-cash protocols [21]. But most promising of all e-cheque system that has the support of major financial institutions and government agencies has been the FSTC’s eCheck system.
Micropayments<
One of the most promising payment methods is the use of micro payments: the ability to pay for data or services in small increments. Micro payments can be seen as a solution to allow low-value payments for purchasing news articles, stock quotes, index queries, per-click purchase and other services over the Internet. In [32], Jones presented some possible micro commerce content providers which are presented in the Table 3.

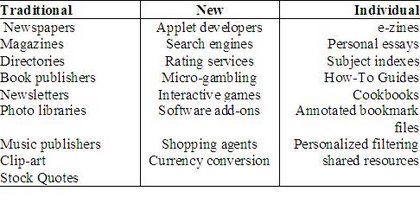
Table 3: MicroPayment Soluctions for content providers
Various micro payment protocols (micromint and payword [33], netbill [31], cybercoin by cybercash, millicent by compaq [34], NetPay [35], and miKP [36]) have been proposed over the years. The primary aim of all micro payment system have been to handle arbitrarily small amounts of money and keep the cost for the individual transaction low along with generic e-payment security requirements like confidentiality, integrity, authentication and non-repudiation.
Mobile Payments
Due to the phenomenal success of mobile communicational devices, there has been increasing effort to used mobile devices as “electronic wallets” to store payment and account information.
Currently two main wireless protocols are used for mobile commerce. WAP (Wireless Application Protocol) [37] developed by WAP forum (consolidated into the Open Mobile Alliance) and iMode [38, 39] developed by NTT DoCoMo, Japan.
WAP is an open and global specification that helps mobile devices with WAP enabled browsers to access information and services. WAP specifications include an XML-type markup language known as Wireless Markup Language (WML) for displaying information on to a mobile device browser. The WAP specifications also include a lightweight protocol stack to reduce bandwidth requirements.
I-mode is a proprietary protocol developed by NTT DoCoMo and uses Personal Digital Cellular-Packet (PDC-P) to provide network services. Imode allows efficient network usage by using packet switching technology for wireless communication and TCP/IP for wired communications. I-mode uses c-HTML (compact-HTML) to display content on mobile devices. I-mode enabled devices are also view HTML web pages as the structure of c-HTML is similar to HTML as compared to WAP where HTML needs to be converted to WML for display.
Both WAP and I-mode provide security features that can be used to provide electronic commerce and electronic payment services.
Others
Polling Schemes:Gabber and Silberschatz [44] and Jarecki and Odlyzko [45], proposed schemes where users register by giving a first payment, which is a signed note including a bank certificate and subsequent payments sent by users are received by the vendor and probabilistically sent to the bank for deposit at the time of the transaction. The overspending risk can be limited to a known value by defining the probabilistic checking as a function of the transaction size (making large payments more likely to be checked).
Phone bases System:BPay [46] and PostBillPay [47] enables users to pay most of your regular monthly bills using either your telephone or your computer 24/7. Bills that can be paid include utilities, telephone bills, cable TV, credit cards, charge cards and many other accounts. To use the system a payee requires to obtain biller specific information (like biller account) and payment details (like credit card information). They also have the option to receive electronic bills for registered users and to send additional details regarding bills registered or add more bills after the initial registration phase.
References
[1] “New payment instruments prototype,” semper deliverable d15, SEMPER Consortium / r3 security engineering (ed.), 1997.
[2] J.A. P.N. Ashokan, “Payment manager-overview,” Tech. Rep. 212ZR054, SEMPER Consortium, March 1996.
[3] J.A. P.N. Ashokan, M.Steiner, and M.Waidner, “Designing a generic payment service,” Tech. Rep. 212ZR055, SEMPER Consortium, September 1996.
[4] N.Asokan, P.A. Janson, M.Steiner, and M.Waidner, “The state of the art in electronic payment systems,” Computer, vol.30, no.9, pp.28-35, 1997.
[5] S.-Y. Choi, D.O. Stahl, and A.B. Whinston, The Economics of Electronic Commerce. Macmillan Technical Publishing, 1997. ISBN: 1-57870-014-0.
[6] N.Heintze and J.D. Tygar, “A model for secure protocols and their compositions,” in 1994 IEEE Computer Society Symposium on Research in Security and Privacy, pp.2-13, IEEE Computer Society Press, 1994.
[7] R.Kailar, “Accountability in electronic commerce protocols,” in IEEE Transaction on software engineering, vol.22(5), pp.313-328, 1996.
[8] M.S. M.W. N.Asokan, PhilJanson, “Electronic payment systems,” Tech. Rep. RZ 2890 (# 90838, 1996.
[9] D.Chaum and H.van Antwerpen, “Undeniable signatures,” in Crypto 90, vol.LNCS of 473, pp.212-216, 1990.
[10] G.Medvinsky and B.C. Neuman, “Netcash: A design for practical electronic currency on the internet,” in First ACM Conference on Computer and Communications Security, November 1993.
[11] M.Card and VISA, SET Secure Electronic transaction protocol, Book 1,2 and 3. available from www.setco.org.
[12] VISA, 3D Secure protocol specification - Core functions. 2002. available from http://international.visa.com/fb/main.jsp.
[13] Master Card, Master Card Secure code - Merchat implementation guide. 2003. available from www.mastercardonline.com.
[14] M.M. Anderson, “Electronic check architecture,” Tech. Rep. Version 1.0.2, FSTC, September 1998.
[15] J.K. (ed.), “Financial services markup language version 1.5,” tech. rep., FSTC, July 1999.
[16] R.Anderson and M.Kuhn, “Tamper reistance - a cautionary note,” in Second USENIX Workshop on Electronic Commerce, (Oakland, California), pp.1-11, November 1996.
[17] P.Kocher, J.Jaffe, and B.Jun, “Differential power analysis,” in Advances in Cryptology - CRYPTO ‘99 (M.Wiener, ed.), vol.1666 of LNCS, pp.389-397, Springer-Verlag, 1999.
[18] D.Boneh, R.A. DeMillo, and R.J. Lipton, “On the importance of checking cryptographic protocols for faults,” in Eurocrypt ‘ 97, vol.1233 of LNCS, pp.37-51, Springer-Verlag, 1997.
[19] D.Chaum, “Blind sigantures for untraceable payments,” in Advances in Cryptology -Crypto ‘82, pp.199-203, 1983.
[20] D.Chaum, “Privacy protected payments - unconditional payer and/or payee untraceablility,” SMARTCARD 2000: The future of IC Cards, IFIP WG 11.6 International conference, Luxenburg, pp.69-93, 1989.
[21] S.A. Brands, “An efficient off-line electronic cash system based on the representation problem.,” in 246, p.77, ISSN 0169-118X: Centrum voor Wiskunde en Informatica (CWI), 31 1993.
[22] D.Chaum and T.Pedersen, “Wallet databases with observers.,” in Advances in Cryptology - CRYPTO’92 (E.F. Brickell, ed.), vol.740 of LNCS, (89-105), Springer Verlag, 1992.
[23] C.P. Schnorr, “Efficient signature generation by smart cards,” Journal of Cryptology, vol.4, pp.161-174, 1991.
[24] VISA and Microsoft, Secure Transaction Technology Specifications. Visa International, version 1.0ed., 1995.
[25] M.Bellare, J.Garay, R.Hauser, A.Herzberg, H.Krawczyk, M.Steiner, G.Tsudik, and M.Waidner, “iKP - A family of secure electronic payment protocols,” pp.89-106, 1995.
[26] Cybercash, GTE, IBM, MasterCard, and Netscape, “Secure electronic payment protocol,” Internet Draft Version 1.2, 1995.
[27] N.Communications, “Ssl 3.0 specification.” http://wp.netscape.com/eng/ssl3/.
[28] “Transport layer security (tls) protocol, version 1.1,” in Internet Draft from http://www.ietf.org/internet-drafts/draft-ietf-tls-rfc2246-bis-08.txt, IETF.
[29] “Mandate.” http://www.cryptomathic.dk/mandate.
[30] B.Neuman and G.Medvinsky, “Requirements for network payments: A netcheque perspective,” in IEEE COMPCON-95, (San Francisco, CA, USA), pp.32-36, March 5-9 1995.
[31] B.Cox, J.D. Tygar, and M.Sirbu, “Netbill security and transaction protocol,” in First USENIX Workshop on Electronic Commerce, (New York), USENIX, July 1995.
[32] R.Jones, “Millicent update - presentation,” presented at e-payment forum, MilliCent Marketing, DEC, San Francisco, March 1997.
[33] R.L. Rivest and A.Shamir, “Payword and micromint: Two simple micropayment schemes,” in Security Protocols - International Workshop, Berlin, Germany, vol.1189, pp.69-88, Springer-Verlag, 1997.
[34] Compaq and Digital, “Millicent homepage.” http://www.millicent.digital.com/.
[35] X.Dai and B.Lo, “Netpay - an efficient protocols for micropayment on the www,” Fifth Australian World Wide Web Confernence, 1999. ausweb.scu.edu.au/papers/technical.
[36] R.Hauser, M.Steiner, and M.Waidner., “Micro-payments based on ikp,” pp.67-82, 1996.
[37] W.Forum, “Wap forum releases.” http://www.openmobilealliance.org/tech /affiliates/wap/wapindex.html.
[38] N.DoCoMo, “Special lssue on i-mode service,” Technical Journal Vol.1 No.1, December 1999.
[39] N.DoCoMo, “i-mode felica,” Technical Journal Vol.6 No.3, December 2004.
[40] R.Anderson, C.Manifavas, and C.Sutherland., “Netcard - a practical electronic cash system,” in Fourth Cambridge Workshop on Security Protocols, Springer-Verlag, 1996. http://www.cl.cam.ac.uk/users/rja14.
[41] T.Pedersen, “Electronic payments of small amounts,” Tech. Rep. DAIMI PB-495, Aarhus University, Computer Science Department, 1995.
[42] C.Jutla and M.Yung, “Paytree: “amortized signature” for flexible micropayments,” in Second USENIX Workshop on Electronic Commerce, 1996.
[43] L.Lamport., “Constructing digital signatures from a one way function,” in Technical Report CSL-98, SRI International, 1979.
[44] E.Gabber and A.Silberschatz, “A minimal distributed protocol for electronic commerce,” in USENIX Workshop on Electronic Commerce, 1996.
[45] S.Jarecki and A.Odlyzko, “An efficeient micropayment scheme based on probabilistic polling,” in Finacial Cryptography’97, vol.1318 of LNCS, Springer-Verlag, 1997.
[46] B.P. Ltd. http://www.bpay.com.au.
[47] A.POST. http://www.postbillpay.com.au/.